Abstract
The Payment Card Industry (PCI) Data Security Standard (DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. PCI DSS provides a baseline of technical and operational requirements designed to protect cardholder data. PCI DSS applies to all entities involved in payment card processing – including merchants, processors, acquirers, issuers, and service providers, as well as all other entities that store, process or transmit cardholder data.
As per the PCI DSS standards 3.6.1, 3.6.2 and 3.6.3, it mandates that the key management processes must cater for archived, retired or compromised keys and this can be achieved by implementing a key management appliance.
As per 3.6.4 and 3.6.5 key-management procedures are implemented to require periodic key changes at the end of the defined crypto-period and the replacement of known or suspected compromised keys. The process of securely storing and replacing these keys is called re-keying and the data stored should be able to attain this feature.
HP P9000 array does not support online re-keying feature and external key management appliance. We can attain these below mentioned solution and helping the customer to be compliance with PCI DSS standards.
Problem statement
Rekeying is the process of rotating or changing the encryption keys for a given data set or first-time migration of existing cleartext (Data without encryption) to ciphertext (Encrypted data). This feature is not supported on HP P9000 Storage arrays.
Depending on key management policies and business practices, data is rekeyed when keys are compromised or their planned, active lifetime expires. The encryption key management is handled by external key management appliances and HP P9000 array does not support external key management.
Solution
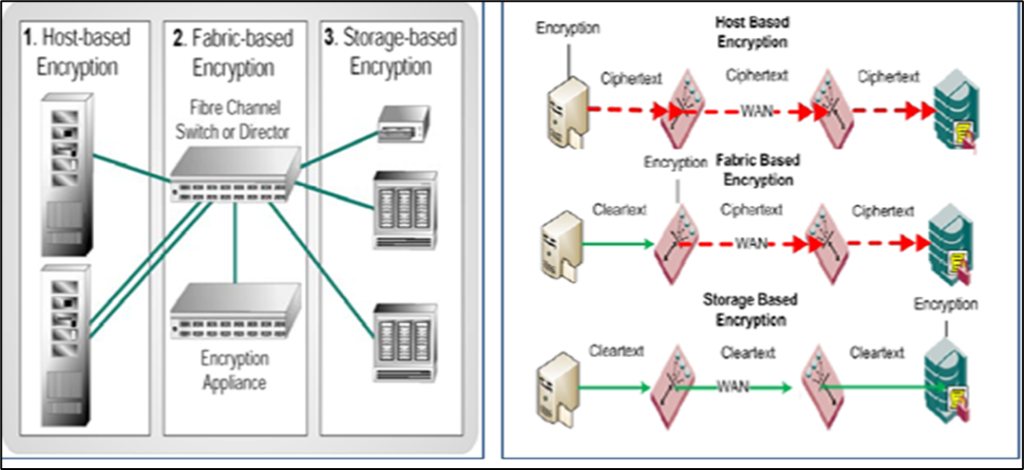
The solution is addressed by configuring HP P9000 (XP24000/P9500) arrays with HP B-Series Encryption SAN switch/Blade and HP Secure Key Manager appliance.
The Encryption Switch is acting as an Encryption Engine to encrypt the data stored in the storage array.
The SKM key vault is used for the Device Encryption Key management.
We can approach this solution for a customer who needs to be compliance with PCI-DSS standards and already has HP P9000 array installed.
Advantages
- Supports online re-keying & key expiry.
- Unparalleled encryption processing at upto 96 Gbps using AES-256 algorithms.
- Supports upto 64K Device Encryption Keys.
- Provides high level compression – GZIP variant before encrypting (addresses tape compression issue).
- Non-intrusive installation into fabric.
- Supports several external key management appliances.
- CC EAL-3 & FIPS 140-2 Level 3 certification.
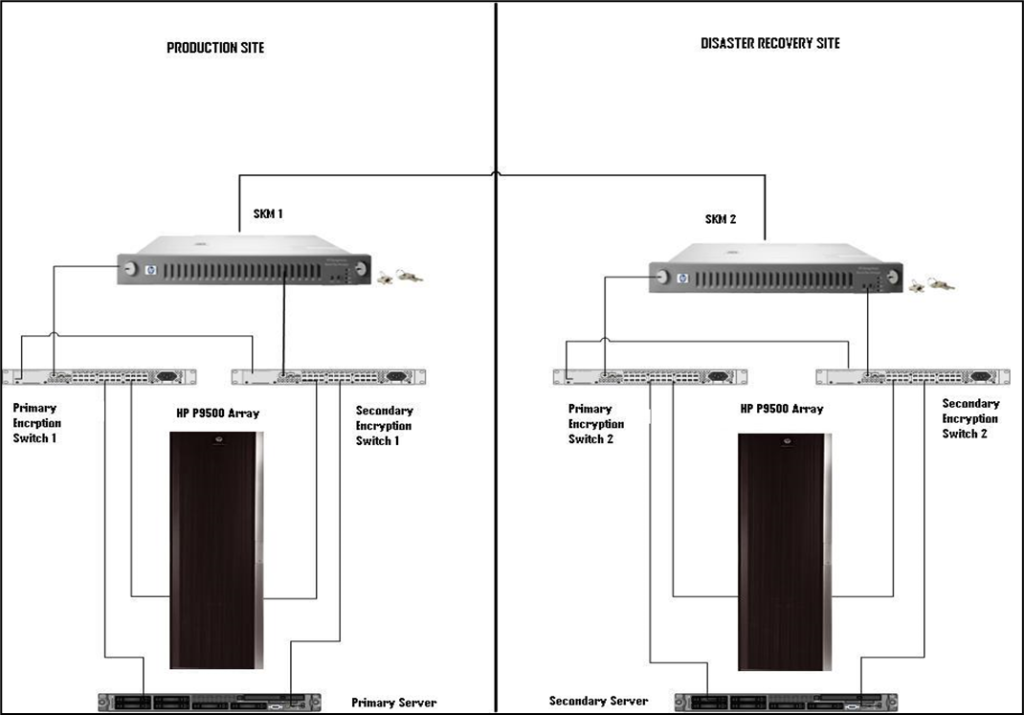
Evidence the solution works
Competitive approaches
The similar encryption feature is obtained by NetApp Lifetime Key Manager (LKM) / RSA Key manager and Brocade Encryption Switches / Blades with Non-HP Enterprise Storage Arrays.
Since it involves different vendors, it increases the complexity in managing the SAN.
Next steps
Customers who are really in a need of using re-keying feature and who are currently using our HP P9000 arrays can able to adopt this solution.
By integrating the feature of online re-keying and extending support to external key management in the Enhanced Disk Adapters (EDKA), we can achieve these features in HP P9000 arrays and also save the cost of an Encryption Switch.
References
SAN Specific Terms
http://www.snia.org/education/dictionary
Payment Card Industry (PCI) Data Security Standard, Requirements and Security Assessment Procedures
https://www.pcisecuritystandards.org/security_standards/index.php
HP P9500 encryption guide
HP Storage Works SAN Encryption Switch
http://h18006.www1.hp.com/storage/saninfrastructure/switches/encrypt_sanswitch/specs.html
HP Secure Key Manager